Frida反调试
一,常见检测
1.ThracePid检测
原理:当被调试器附加之后 不为0:安卓逆向反调试的手段有哪些-街头小贩
检测方法可以一直遍历 /proc/self/status Thracepid的值
ptrace占坑:
https://bbs.pediy.com/thread-268155.htm#msg_header_h2_16
(具体方法见ida动态调试部分有详细记录,这里我们就跳了)

2.进程名检测
遍历进程名是否包含frida-server
[翻译]多种特征检测 Frida-外文翻译-看雪安全社区|专业技术交流与安全研究论坛
3.端口检测
27042是frida的默认端口
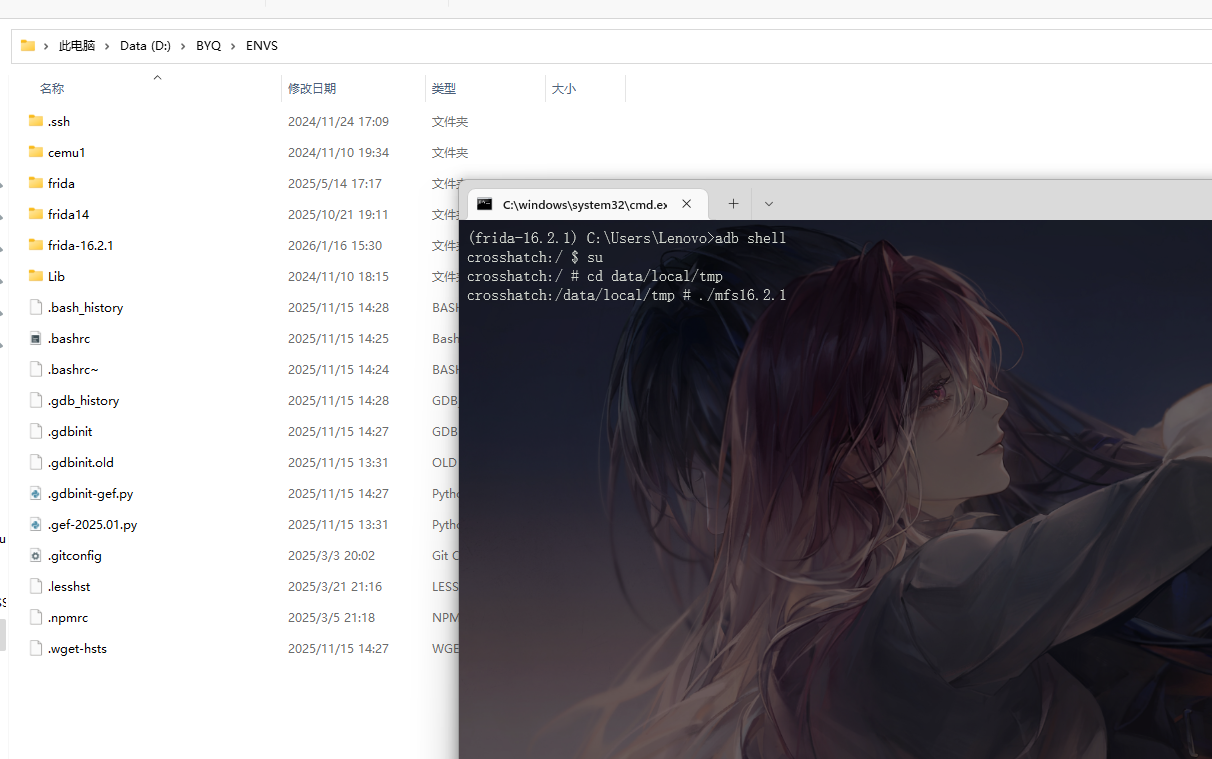
./fs1 -l 0.0.0.0:6666
adb forward tcp:6666 tcp:6666
frida -H 127.0.0.1:6666 包名 -l hook.js
4.D-Bus协议通信
文章:https://bbs.pediy.com/thread-217482.htm
因为fridaserver 使用D-Bus 协议通信,我们为每个开放的端口发送D-Bus 的认证消息,哪个端口回复”REJEcT”.哪个就是fridaserver。
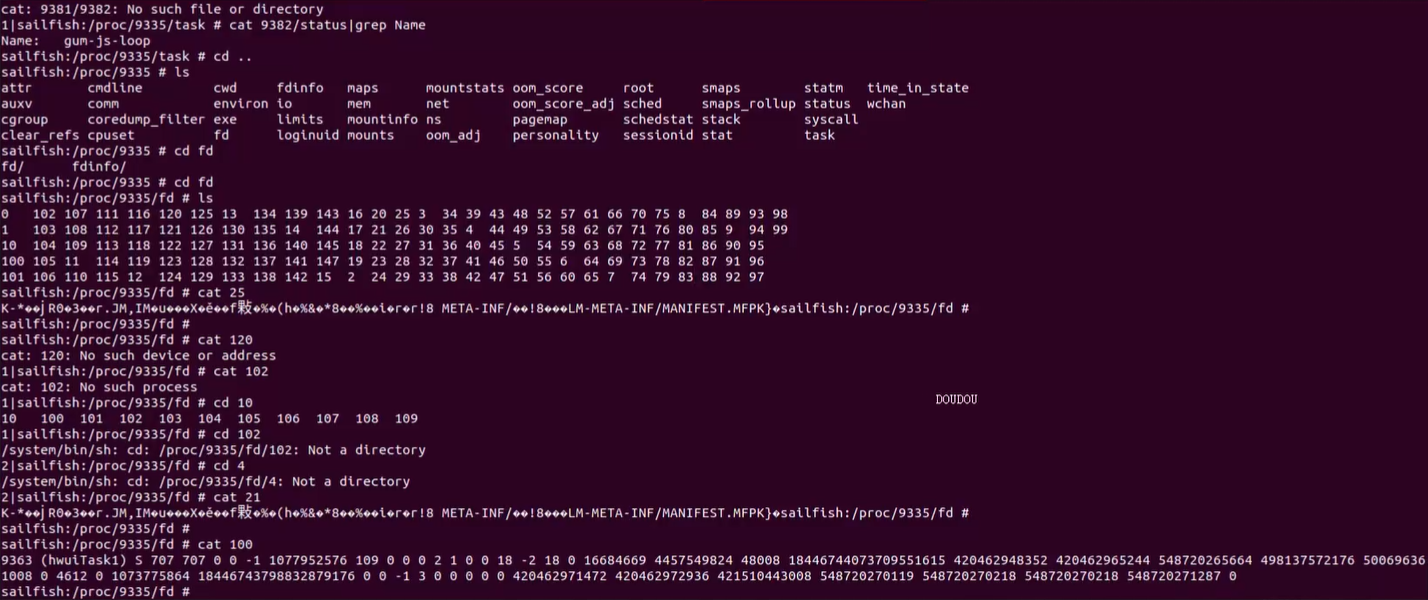
5.maps检测
/proc/self/maps 是一个特殊的文件,它包含了当前进程的内存映射信息。当你打开这个文件时,它会显示一个列表,其中包含了进程中每个内存区域的详细信息。
adb shell dumpsys window w lgrep V lgrep name=
先搜索一下进程
ps -e | grep 包名
cat proc/进程号/maps | grep frida

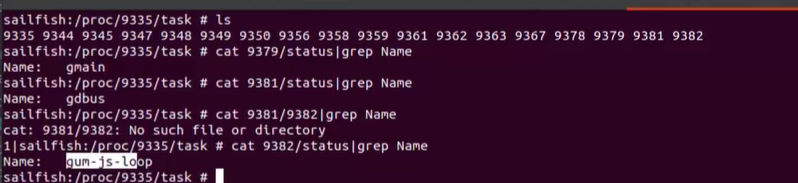
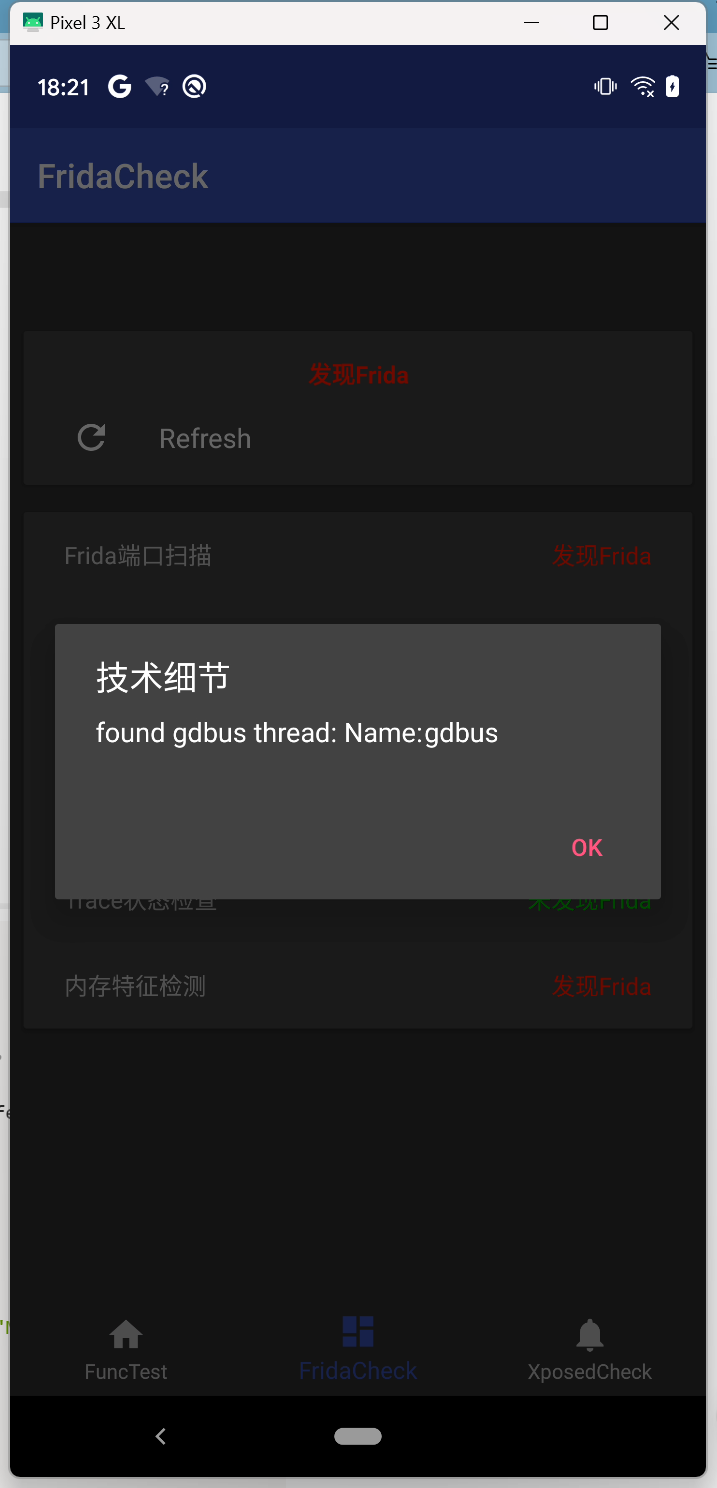
6.线程检测gmain,gdbus,gum-js-loop
sailfish:/proc/进程号/task
cat 31651/status|grep Name
Name:
gdbus
/proc/self/task/self/status
7.内存特征检测frida相关的字符串
8.自实现的比较函数
二,过检测的几种方式
下面以Demo示例
adb shell dumpsys window | findstr mCurrentFocus
运行查看包名
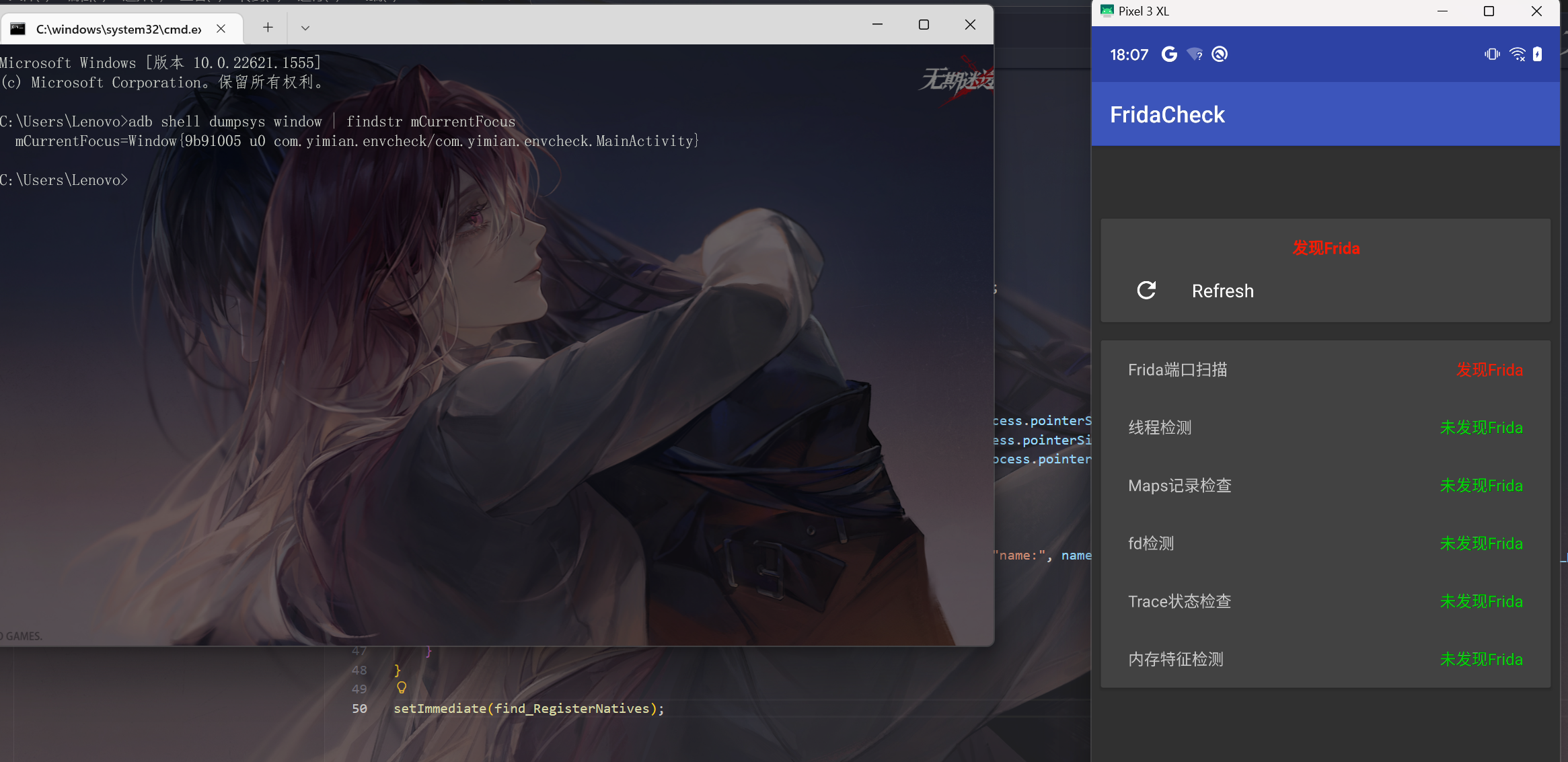
我们将apk扔进jadx发现检测均为native函数,我们hook so层
借助脚本定位检测frida的so
1 | |
偏移
1 | |
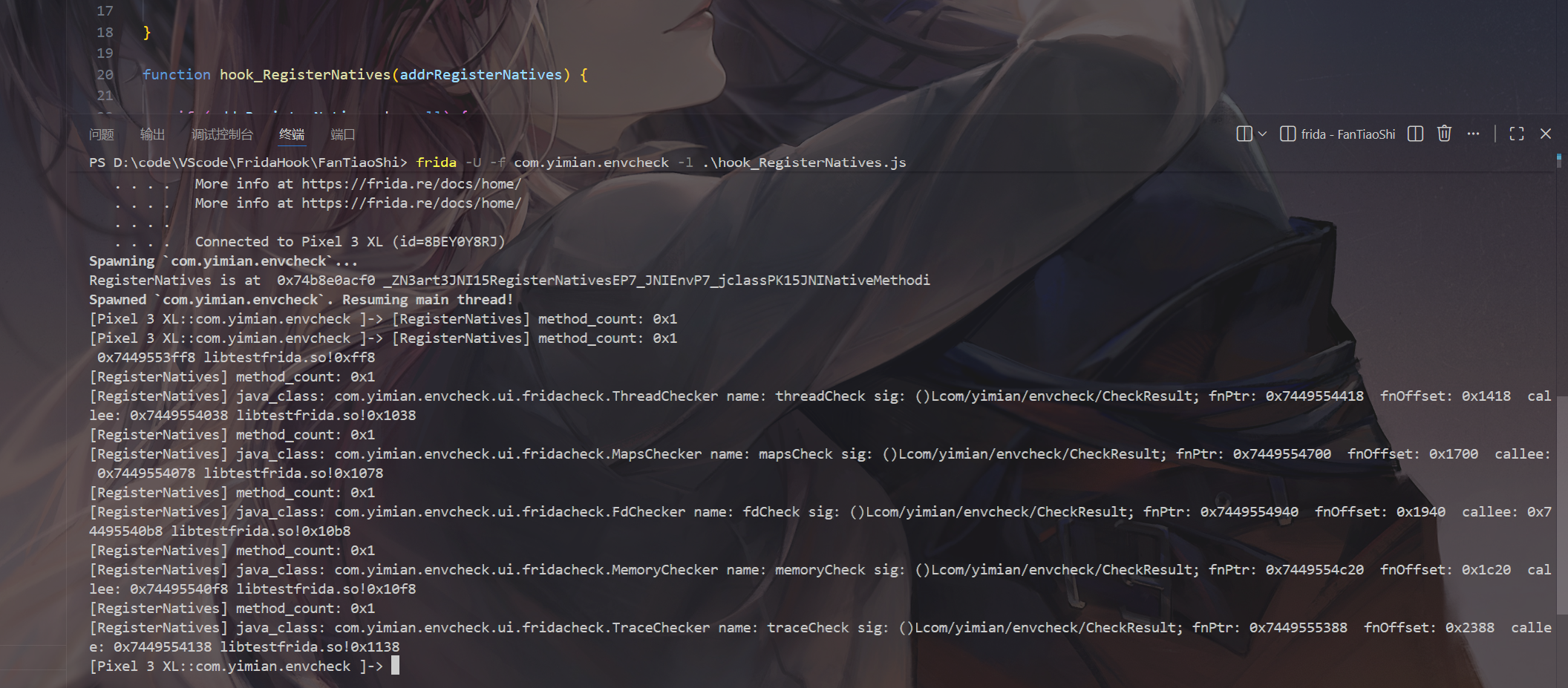
我们通过ida查询偏移
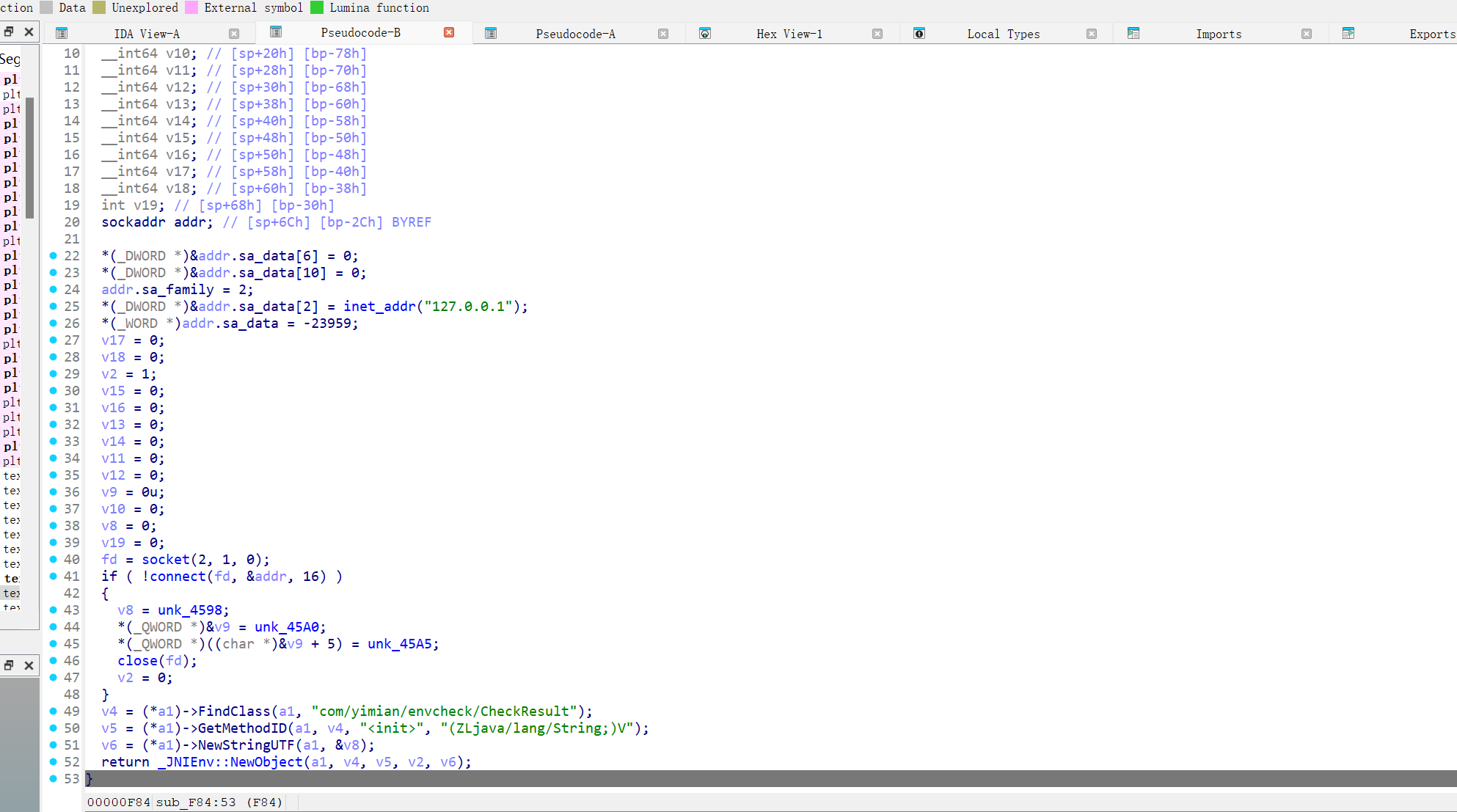
我们就找到了第一个检测点,直接修改过掉就可以
ThracePid反调试
android拦截native方法,Android native反调试方式及使用IDA绕过反调试-CSDN博客
1 | |
hook线程创建
定位检测点hook系统函数进行过掉需要分析常用于检测的系统函数
线程检测反调试
我们ida跳转到0x10b8
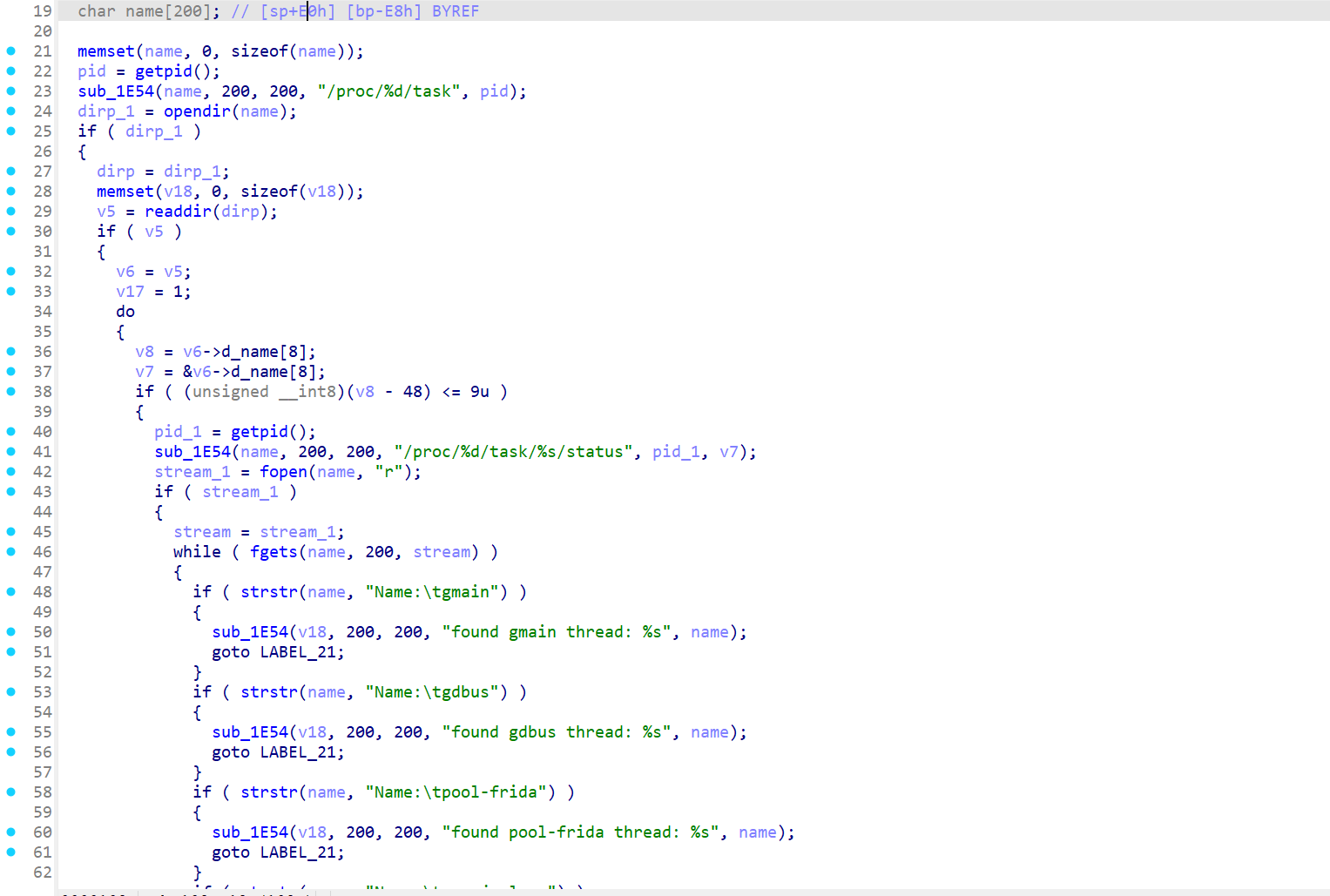
我们可以发现线程检测就是
我们通过返回假,来过掉检测
1 | |
成功过掉线程检测
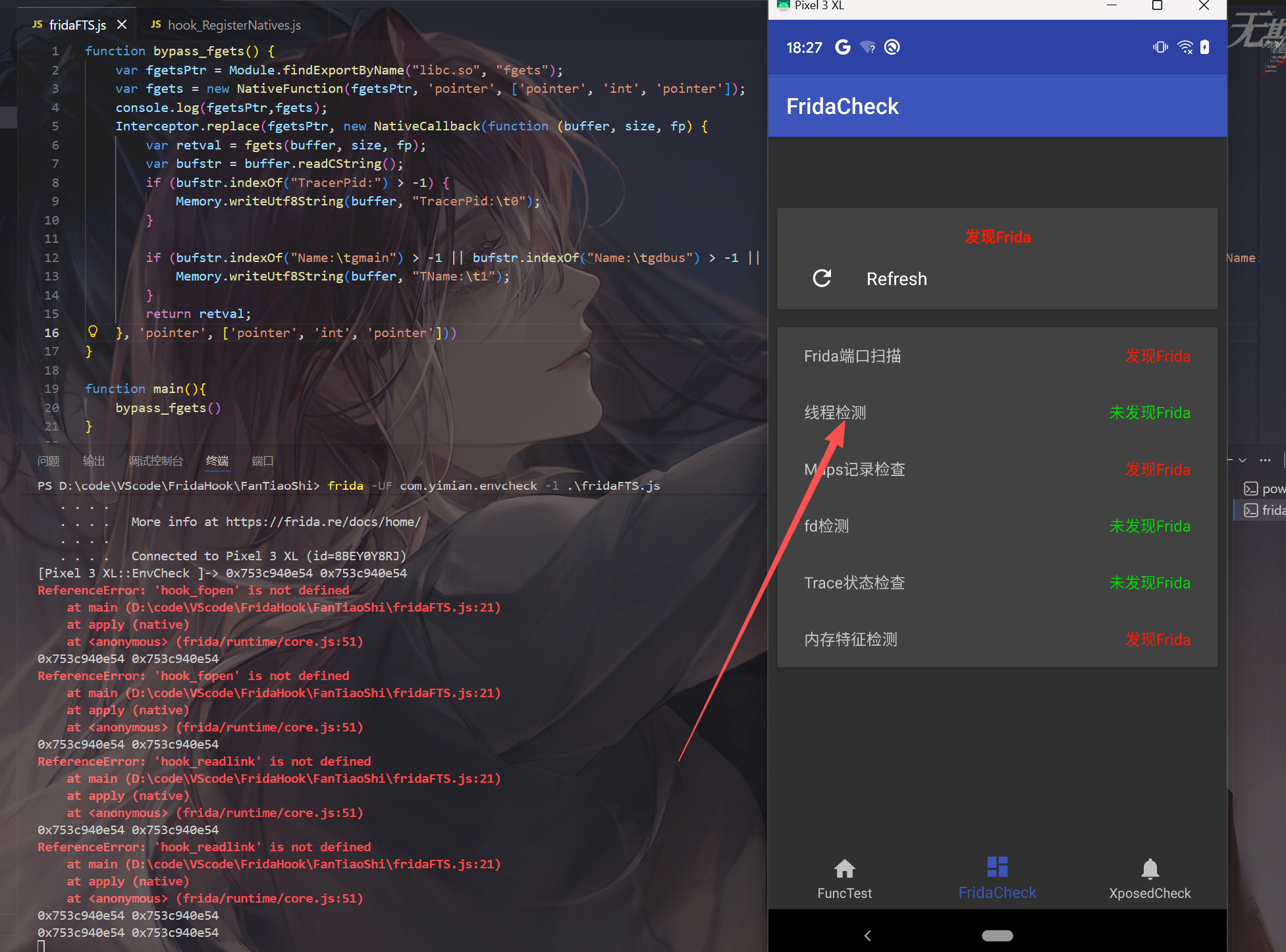
除了hook fgets我们该可以hook strstr再或者hook fopen
过maps检测
1 | |
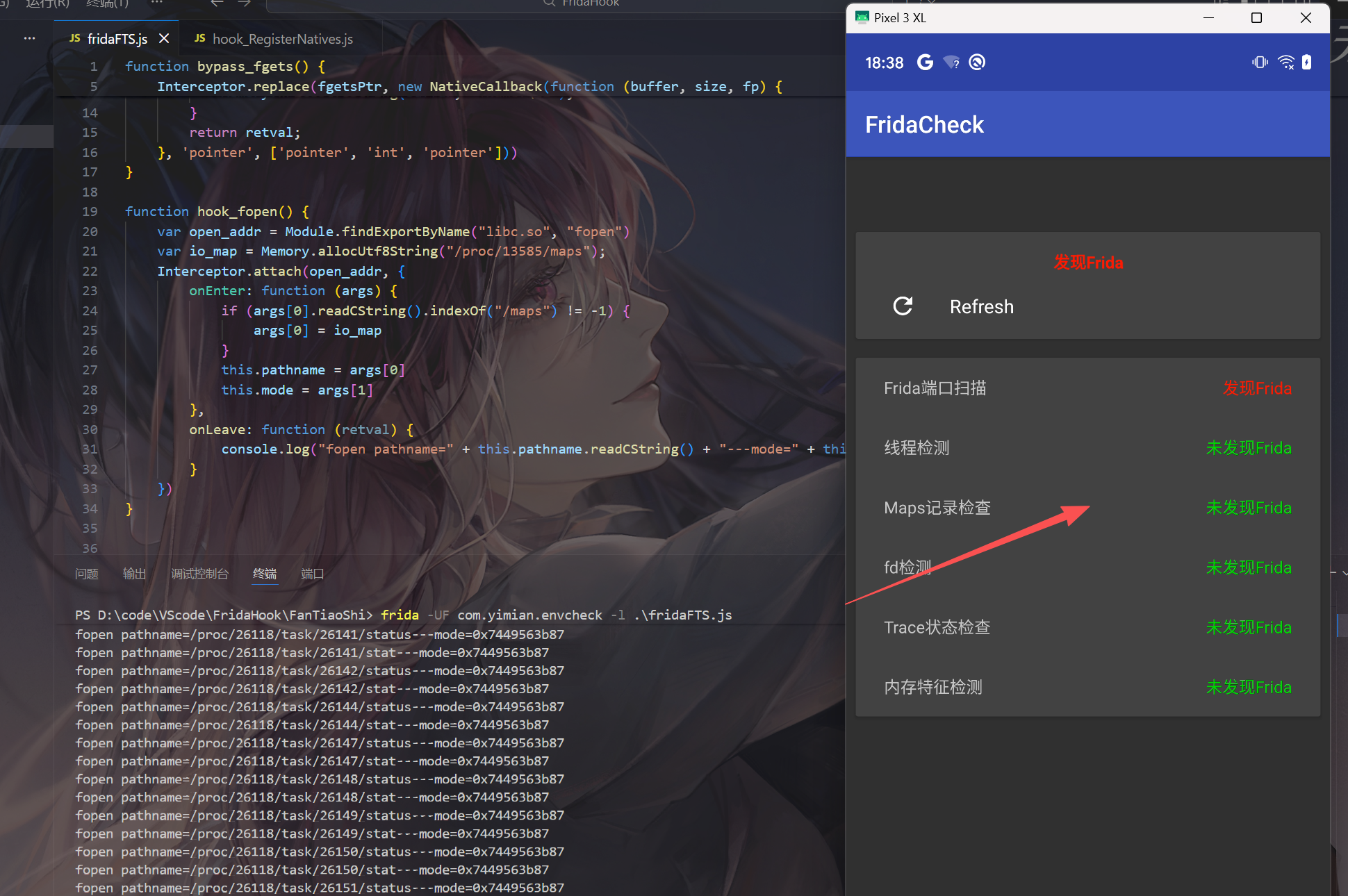
过FD检测
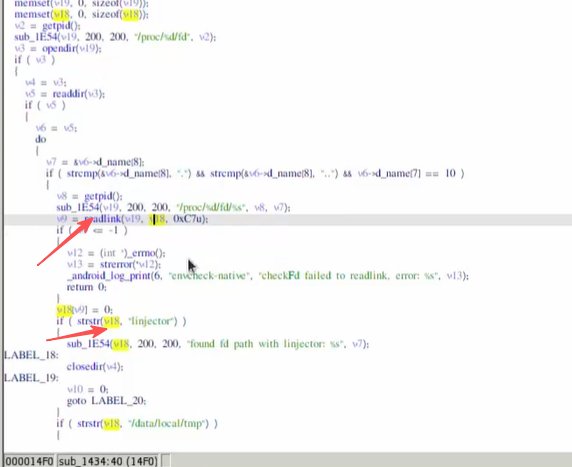
readlink()会将参数path的符号链接内容存储到参数buf所指的内存空间,返回的内容不是以\000作字符串结尾,但会将字符串的字符数返回,这使得添加\000变得简单。若参数bufsiz小于符号连接的内容长度,过长的内容会被截断,如果 readlink 第一个参数指向一个文件而不是符号链接时,readlink 设 置errno 为 EINVAL 并返回 -1。 readlink()函数组合了open()、read()和close()的所有操作。
1 | |
魔改frida
https://github.com/taisuii/rusda
[undetected-frida] https://github.com/zer0def/undetected-frida
[strongR-frida-android] https://github.com/hzzheyang/strongR-frida-android
[Florida] https://github.com/Ylarod/Florida
[rusda] https://github.com/taisuii/rusda
实战过检测
1.hook线程创建干掉检测线程案例
i加密的 贵旅
我们去hook创建,当线程加载的时候会挂掉,打印出相应的so以及偏移
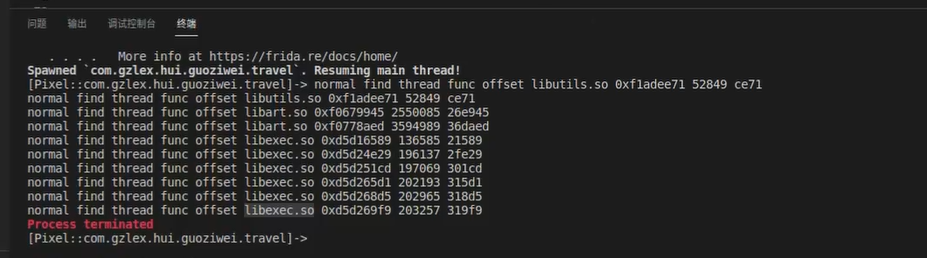
我们吧其中不要的偏移hook掉
1 | |
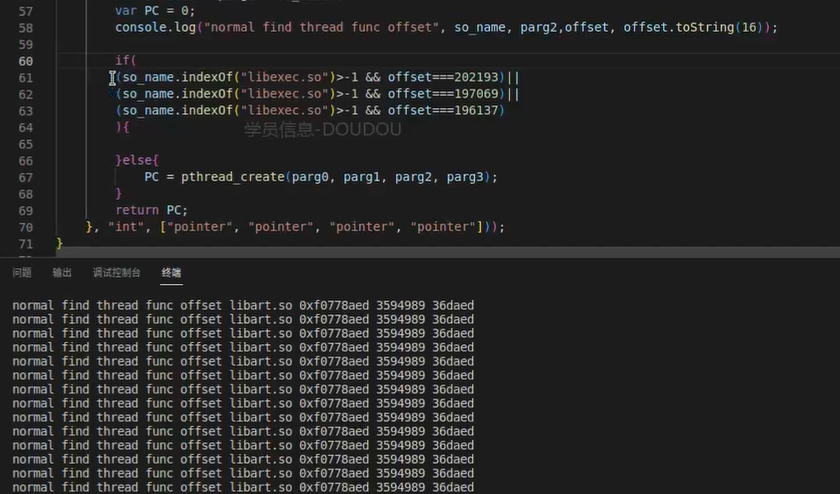
排除后就找到相关文件。
梆梆 步道悦跑
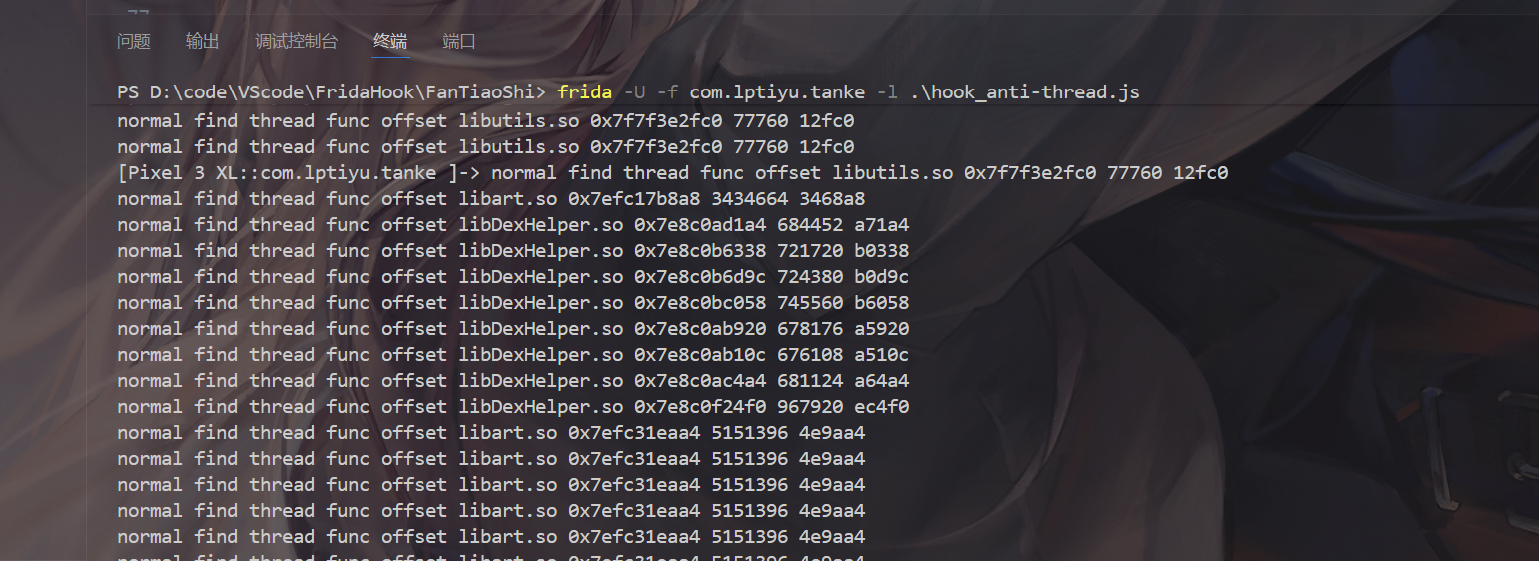
同理hook排除得到libDexHelper.so线程干掉即可
2.定位检测点 hook系统函数进行过掉
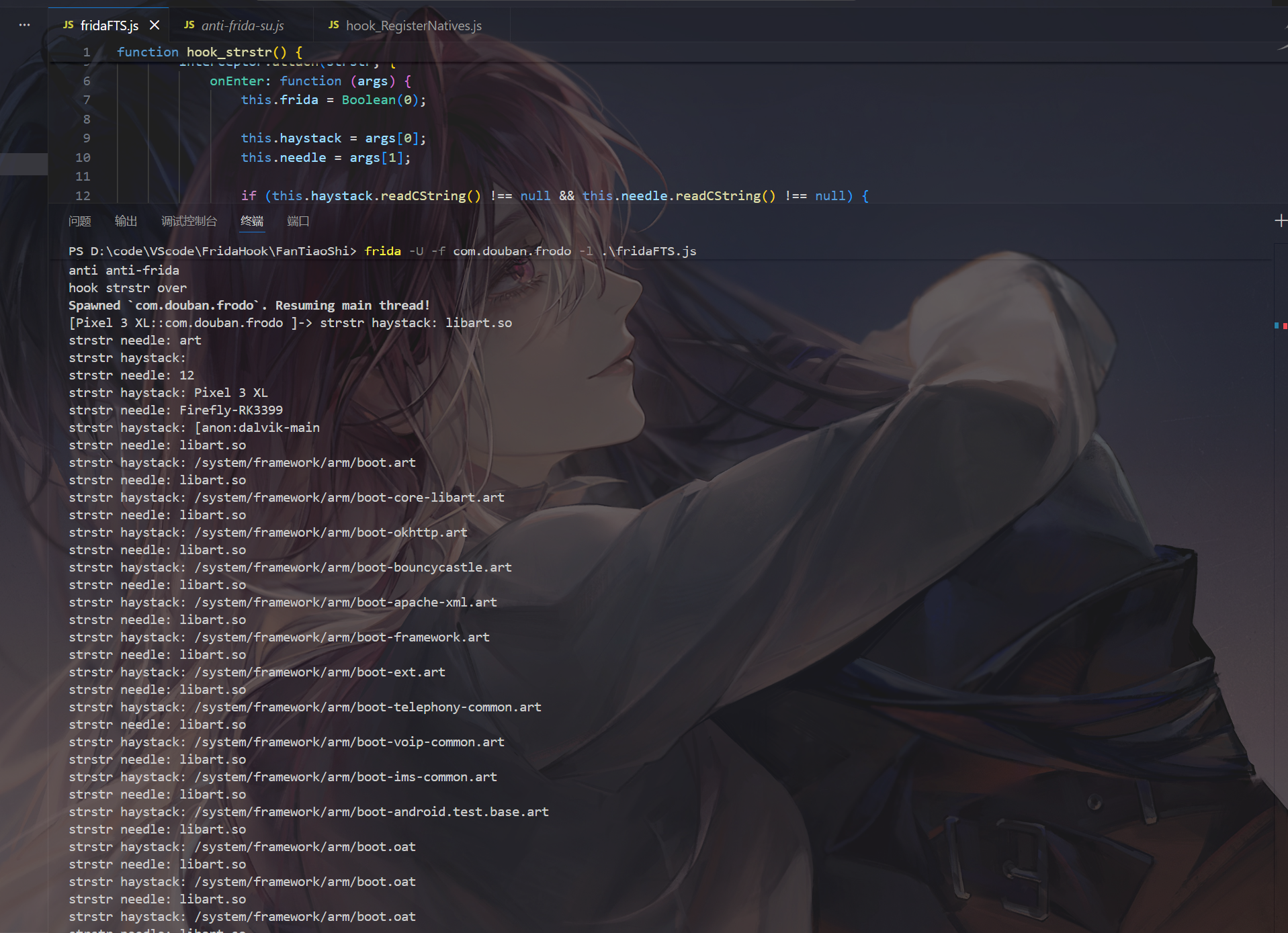
需要分析 常用于检测的系统函数:strstr,strcmp.open,read.fread,
豆瓣
1 | |
3.魔改frida将frida的特征都给改完仿照葫芦娃加上自己的
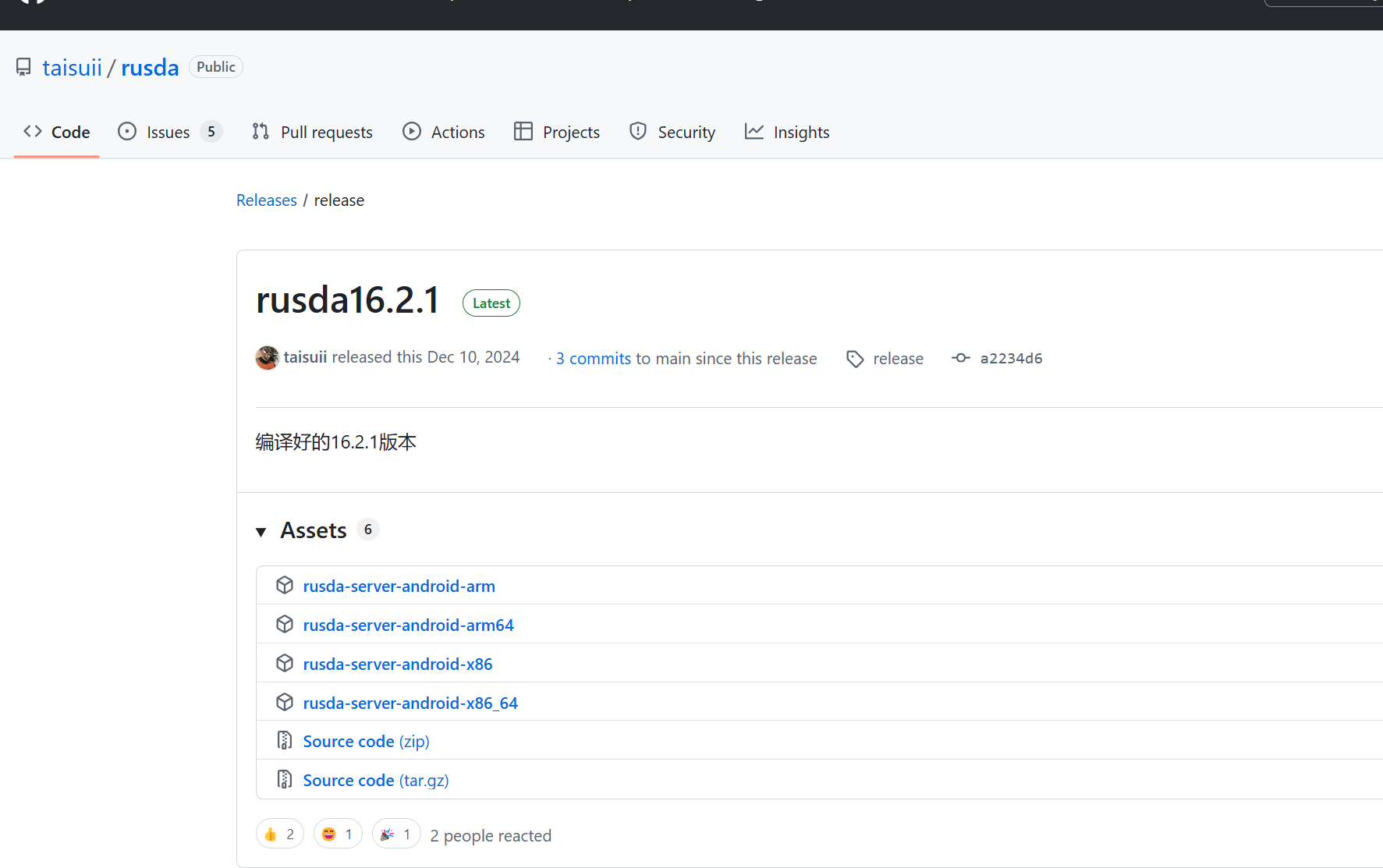
我们直接使用魔改好的frida就可以绕过大部分检测,魔改新老版本差别较大我们后续有空单独探讨。